BlueRiSC DFI New Article (Digital Forensics Investigator): Hardware-Assisted Advanced Forensics and Cyber Threat Detection
BlueRiSC DFI New Article (Digital Forensics Investigator): Hardware-Assisted Advanced Forensics and Cyber Threat Detection https://www.bluerisc.com/wp-content/uploads/2014/12/iStock_000009090323_Medium-1-1024x682.jpg 1024 682 BlueRiSC https://secure.gravatar.com/avatar/a7158cc1d3cf99ba24bb066e9343643b?s=96&d=mm&r=gThe goal of any computer investigation is to obtain as much evidence as possible from the computer, while at the same time ensuring the integrity of the evidence. It is equally important that investigators are able to find the needed evidence as quickly as possible. Investigation efforts are drastically slowed by privacy and security measures, such as login passwords and full disk encryption, which have become all-too-common in modern personal computers [1]. In addition, stealth rootkits and other anti-forensic techniques further interfere with evidence collection. This article will describe some core capabilities that are necessary for overcoming these obstacles in investigations: bypassing login passwords, physical memory acquisition, relevant virtual memory acquisition, memory reverse engineering, space-time analysis/anomaly detection, and custom analysis and integration support.
Bypassing Login Passwords
When encountering a powered on system, live forensics is the only way to preserve the full state of a system. It allows investigators to capture valuable data from DRAM, which is otherwise lost if the computer is unplugged or shutdown. In computers with encrypted volumes, live forensics is often the only means of obtaining the encryption keys for the disk, since the keys are present in memory while the system is running [2]. The main difficulty with live forensics, however, is that it requires being able to login to the computer. Investigators rarely have the password to the computers they examine, so they require a method to login without knowing the password.
Hardware devices, such as the CaptureGUARD Gateway ExpressCard are able to bypass login passwords without restarting, by using direct memory access (DMA) to disable the password protection mechanism[3]. With the password protection disabled, the investigator can login to the computer to perform live forensics, which may include physical memory acquisition, virtual memory acquisition, and extracting data from file systems. While logged in, the investigator will typically have full access to encrypted volumes including those managed by BitLocker. The file system can either be investigated while the system is live, or the encryption keys can be extracted from a memory image and used to investigate the encrypted disk offline.
Physical Memory Acquisition
Once the password has been bypassed, the investigator has full access to the computer, allowing them to gather any evidence necessary, including the contents of the DRAM in the system. The most common method of acquiring a memory image is to run a small program that reads the contents of physical memory and stores it to a file, usually located on a removable drive. One problem with this method, however, is that running the memory dumping software on the computer being investigated leaves behind a memory footprint, modifying some of the data in the evidence being collected. Another problem is that rootkits can hide or modify memory contents, preventing software memory acquisition tools from creating an accurate memory image. A better approach is to use a PCI Express or ExpressCard device like CaptureGUARD for memory acquisition [3]. Since the PCI Express bus connects directly to the DRAM, hardware devices connected to it can acquire a memory image without having to run any software on the host system. This means that a memory dump can be acquired without affecting the evidence at all. FireWire is also capable of performing DMA, but has limitations in its ability to access physical memory. FireWire is only able to access the low 4GB of system memory, and in many cases, accessing certain memory locations can crash the system [4]. The CaptureGUARD ExpressCard for memory acquisition is shown in Figure 1.
Relevant Virtual Memory Acquisition
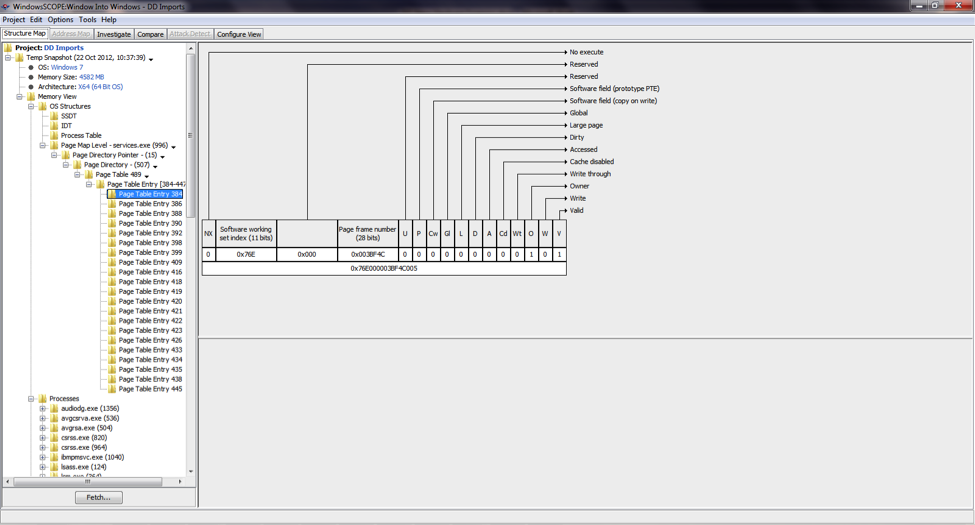
After a physical memory dump has been acquired, the investigator can afford to be somewhat more invasive, in order to get as much information as possible while the system is still live. At this point the investigator can perform relevant virtual memory acquisition, a feature supported by tools such as WindowsSCOPE Ultimate [3]. The relevant virtual memory consists of memory contents that have been paged to the disk in addition to data that was present in the physical memory dump. Also, through the use of the page tables, it can be shown which memory contents were already present in physical memory and which contents had to be paged in during the acquisition. Figure 2 shows a highlighting feature that can be used to easily identify which pages were present and non-present in physical memory before a virtual memory fetch.
Memory Reverse-Engineering
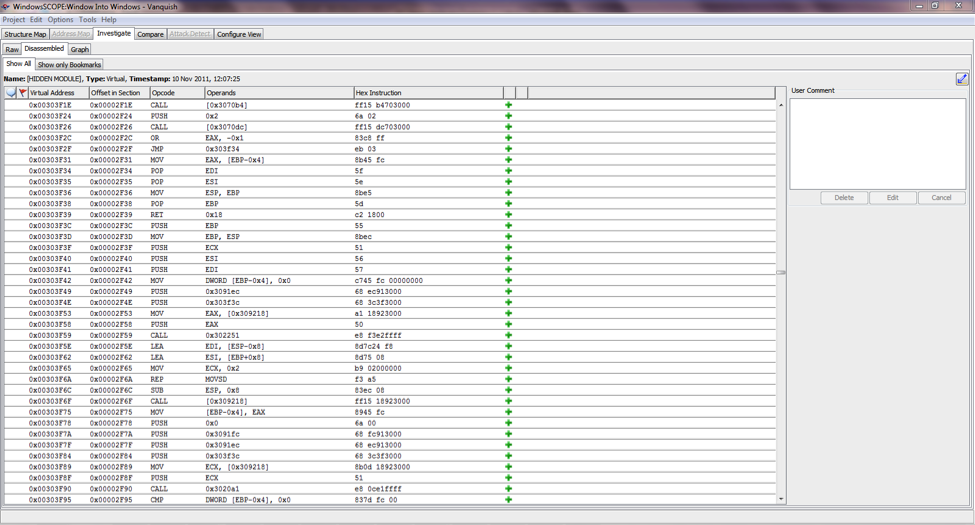
Once the live data has been extracted from the system it can be taken off-site to be analyzed. Due to the fact that x86 processors use a virtual memory architecture with paging, getting meaningful information from a physical memory dump requires an involved reverse-engineering process. The operating system works together with the x86 processor to give each process its own view of memory, called its virtual address space. The operating system creates a set of page tables for each process, which the processor uses to translate virtual addresses into physical addresses. To reverse-engineer a physical memory dump, the page tables for each process need to be found. Then the page tables can be used to reconstruct the virtual address space of each process that was running when the image was acquired. Figure 3 shows page tables that have been reverse-engineered from a physical memory dump.
There are 3 different x86 paging schemes – 32-bit addressing without physical address extension (PAE), 32-bit addressing with PAE, and 64-bit addressing. Although these paging schemes are all similar, the slight differences between them can complicate the memory reverse-engineering process if the exact scheme in use is unknown. Fortunately, memory analysis tools such as WindowsSCOPE Ultimate can examine physical memory dumps and automatically detect the architecture and operating system from the memory dump [3].
Space-Time Comparison/Anomaly Detection
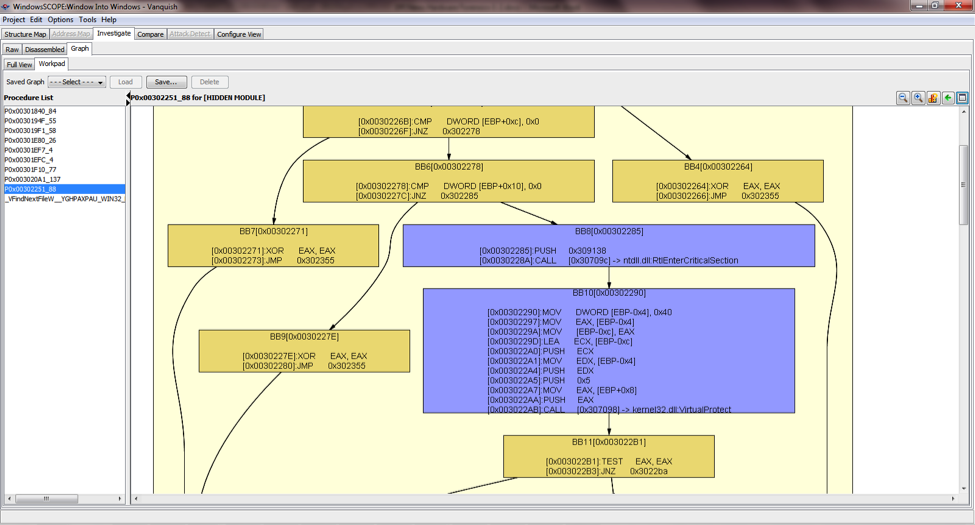
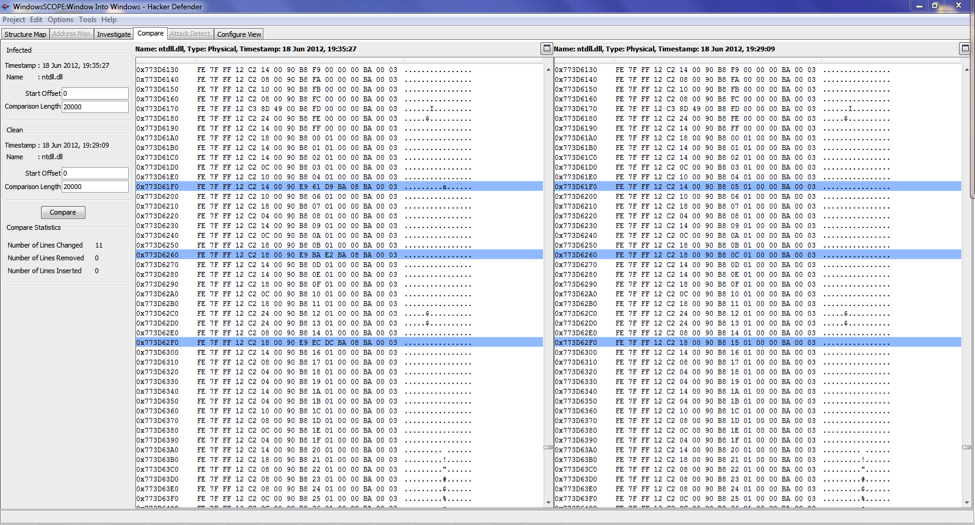
During the reverse-engineering process tools may translate memory dumps into a forensics intermediate format enabling efficient analysis of forensic artifacts by saving the result of the reverse-engineering process and allowing the investigator to add annotations. Typical information of interest stored in intermediate format includes the interrupt table, system service table, process table, handle tables, thread tables, and all sections of executable code on the system. These pieces of information can be used for detailed intra-snapshot analysis techniques such as code disassembling and control flow graphing, shown in Figures 4 and 5. In addition to intra-snapshot analysis, several memory snapshots can be stored in a repository, which also enables inter-snapshot analysis, such as space-time comparison. In space-time comparison, snapshots taken from different computers over a span of time can be stored in the same repository and compared. Figure 6 shows a space-time comparison in WindowsSCOPE detecting an anomaly that resulted from a rootkit modifying operating system code. With snapshots taken at regular intervals on several different computers, it becomes possible to detect exactly where and when anomalies appear.
Comparison between Methods of Memory Acquisition
Due to the nature of advanced stealth rootkits, not every memory acquisition method is effective at detecting all types of threats. For example, there are rootkits known to subvert the virtual memory architecture, whereas others hook operating system APIs that may be used for acquisition. To adequately detect different types of threats, memory snapshots acquired by various different methods can be added to the repository. Different acquisition methods that can be used include software based physical memory acquisition, hardware based physical memory acquisition, and related virtual memory acquisition.
Custom Analysis and Integration Support
One final capability required by investigators and incident responders is custom analysis and integration support. Investigators and incident responders need tools that work with standard formats and can expose an API to their library of analysis features. This allows them to perform their own custom analysis, integrate their tools into their own custom flows, and add automation and scripting to their tools. Open source tools are fragmented and do not provide several of the key capabilities mentioned above. Some commercial tools like WindowsSCOPE support extensions and custom analysis while also providing a better-integrated experience and more advanced feature set.
Figures